For years, we’ve heard the same advice on how to unlock higher levels of cybersecurity greatness. We’re here to tell you that these well-meaning cybersecurity tips have turned into background noise, the kind of guidance that gets a thumbs-up emoji, and not much more.
While these suggestions aren’t totally wrong, they're way too vague to be actionable, too old to be relevant, or just plain unrealistic. When cybersecurity advice doesn't connect with real-world behavior, you get served a false sense of security with a side of potentially serious vulnerabilities.
Let’s break down some of the most overused cybersecurity tips and share what you should do instead: redefine the offensive game and get disruptive on attackers.
"What's the most elegantly offensive thing you've done to wreck a hacker's game plan?" (video originally posted to LinkedIn)
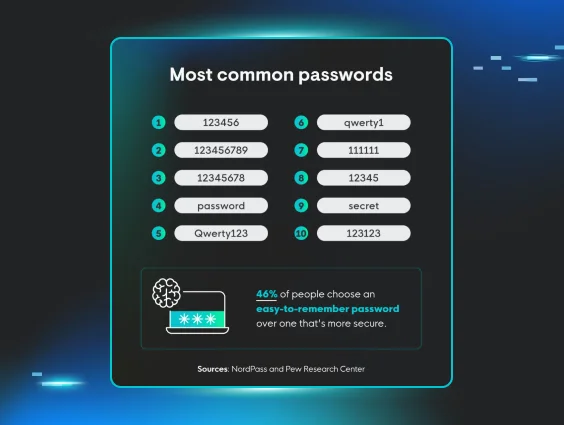
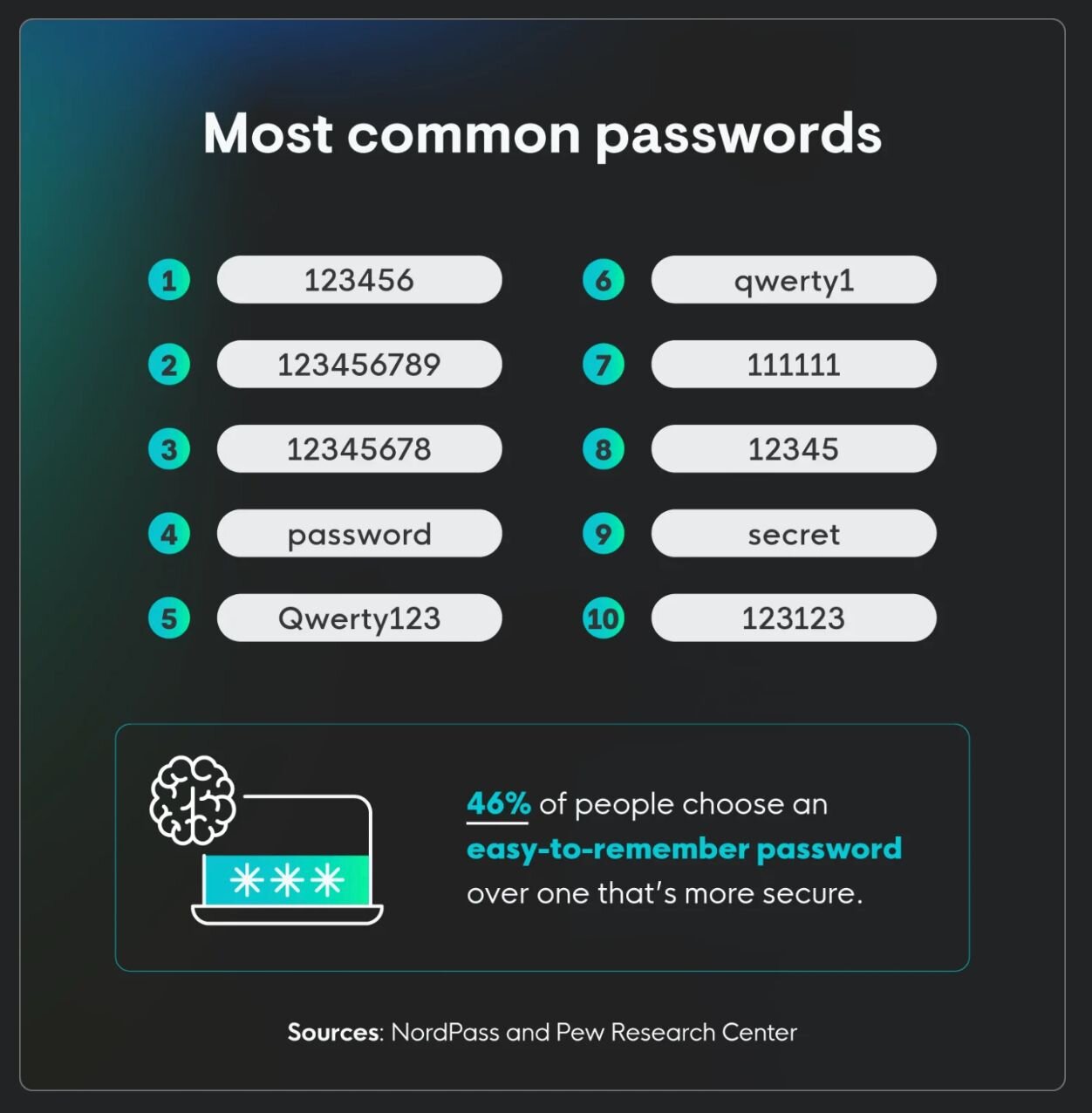
"Use a strong password" (you mean, a pet’s name + an exclamation point isn’t secure?)
If there were a contest for most popular cybersecurity tips, this would bring in the blue ribbon year after year. You’ll catch this phrase in nearly every security awareness training, but password security isn’t about throwing out a capital letter, a number, and a special character anymore.
Attackers have access to sophisticated password-cracking tools and dark web markets full of cheap, compromised credentials, so you have to step up your password game to stay safe online.
Here’s another option: Use password managers to generate long, random passwords automatically. Go with the NIST standard of password security: a minimum of 15 characters, with emphasis on length over complexity. At 100 billion guesses per second, it would take a computer more than 500 years (!) to guess all the possible combinations of 15 lowercase letters.
For those who rely on "familiar phrases" that can be easily hacked, password managers take the human element out of the equation. As a user, keep tabs on one strong master password, and the manager handles everything else, solving problems like weak passwords, reuse, and memorization hiccups.
By the way, throughout Cybersecurity Awareness Month, we’re giving you free access to episodes of select Managed Security Awareness Training (SAT). Check out this one on secure passwords:
"Don't click suspicious links" (...but what if nothing looks shady?)
Modern phishing attacks have leveled up in a major way. Almost gone (but not quite!) are the days of phishing emails brimming with spelling and grammar errors, sloppy designs, and strange phrases.
Attackers now create realistic email replicas of legitimate businesses, complete with polished branding, SSL certificates, and URLs that closely mimic real domains. Simply telling people to avoid "suspicious" links assumes they can easily spot sophisticated social engineering attempts.
Try this instead: Teach and encourage email verification techniques. If someone receives an unexpected link or attachment, especially one requesting login credentials, they should verify it through an independent channel. This means calling the sender, logging into accounts directly through bookmarked sites, or using separate communication methods to confirm legitimacy.
It’s also critical that employees know how to report phishing attempts, so that the right people in your organization are aware and can take action.
Learn to stay ahead of social engineering scams with these free Managed SAT episodes:
"Keep your software updated" (skip automation if you like getting hacked)
Software updates are critical for security and keeping attackers on the outside, but asking people to manually check for and install updates across dozens of applications and operating systems is unrealistic.
People don’t update because they're busy, overwhelmed, putting out fires, or just forget until it's too late.
Do yourself a favor: Rely on automatic updates wherever possible, especially for operating systems, browsers, and security applications.
For enterprise environments, get centralized patch management systems that handle updates systematically. This takes human oversight out of the equation and keeps security patches rolling smoothly.
"Install antivirus" (signature-based detections only go so far)
Traditional antivirus (AV) software was built for an old-school threat landscape. Attackers know it’s ready and waiting to block malicious signatures and light up your dashboards. So they rely on tactics like fileless malware, Living Off the Land (LOLBins) techniques, or sneaky ransomware that dodges signature-based detection altogether.
Here’s another approach: Combine Managed Endpoint Detection and Response (EDR) capabilities with Managed Microsoft Defender to sniff out shady attackers roaming around your systems and networks. Get offensive and give yourself an unfair advantage against hackers.
"Don't reuse passwords" (because hackers love it when you do)
This advice is good, but it isn’t practical for most people to follow without a password manager. On average, people have 168 passwords for personal use and 87 for business-related accounts. Each of these should have an individual, unique, and secure password. Sounds really ambitious without help from a password manager, right?
So if your banking password slowly crept into other accounts for convenience, or you’re recycling passwords across work and home devices, it’s a good time to rethink your password security strategy or create one altogether.
Check this out: Password managers solve this problem (see above). Rather than expecting superhuman memory skills and magic, give people tools that make good password hygiene effortless. This turns a seemingly impossible chore into a manageable task.
"Turn on MFA" (text codes aren’t the only option?)
“Turn on multi-factor authentication” is great advice, but it usually stops there without explaining the different options to keep yourself safe.
Not all MFAs are created equal. Sure, a text message code is better than nothing, but it’s easy for attackers to get around. App-based authentication (like Authenticator or Duo) or physical security keys offer stronger protection and are much harder to compromise.
Turn it up a notch: Recommend app-based authenticators like Authy, Google Authenticator, or Microsoft Authenticator as the baseline. For high-value accounts, suggest hardware tokens like YubiKeys.
If people are grumbling about a few extra steps that security imposes, explain how easy it is for attackers to compromise SMS-based MFA completely under the radar and what this means for their privacy or lack thereof after an intrusion.
Learn why MFA keeps you more secure online with this Managed SAT episode:

"Lock your screen" (but hackers hope your accounts stay wide open)
Screen locking and physical security are good habits, but it doesn’t (and never will) measure up to the risk of cyber threats in most corporate environments. With remote work, cloud storage, and mobile devices, network-based attacks are more likely than threats stemming from physical access to a workstation.
Mathematically, your digital attack surface is a lot bigger than the physical one. So, attackers have infinitely more opportunities to wreck your systems with cyber versus physical intrusions.
Shift your perspective: Don’t ignore things like screen locks and shoulder surfing. But don’t make them the main focus either. Bring them into awareness scenarios that cover network security hygiene and align with your workforce. For example, if you’re a fully remote business, consider discussions on secure wifi, risks of public networks, and keeping your laptop screen low-key in public places.
"Change your password every 30, 60, or 90 days" (so hackers can set their calendar reminders, too)
Forced regular password changes don’t actually help your security posture. Realistically, here’s what people do when they have to change passwords too often:
-
Create predictable (easily hackable) patterns
-
Rely on small changes to existing passwords (think swapping a single character or letter)
-
Store them haphazardly
This is just another way hackers get potentially ridiculously easy access to your systems and networks.
Listen to the pros: NIST says reset passwords if you suspect you’ve been compromised. Otherwise, drop your mandatory password reset rules!
"Cybersecurity is everyone's responsibility" (it’s not just for IT nerds anymore)
Everyone in a business helps with cybersecurity, not just IT. Whether you work in human resources, legal, marketing, or any other department, you contribute to your organization’s security posture every day.
But truly making cybersecurity everyone’s responsibility means regular communication to highlight actions that protect not just you, but also the whole team. Without the right resources, training, or tools, people don’t get a fair shot at being successful human firewalls.
Be a resource, not a roadblock: Give people what they need to keep a business safe from hackers: knowledge, resources, and authority to confidently make good security decisions and safely report sketchy activity without blame.
"Be careful online" (vague is your color, and you wear it well)
The least helpful cybersecurity advice award goes to “Be Careful Online!” There’s NO actionable guidance, and this could mean absolutely anything. Without real-world suggestions for improvement, this is meaningless security jargon that goes in one ear and out the other.
Give this a shot: Teach people how to spot common cyber threats like phishing attempts, malicious websites, malvertising, and social engineering tactics with tools like ad blockers and Managed SAT.
Turn lame, overplayed cybersecurity best practices into action
People are an organization's strongest defense, but also its easiest target. Effective cybersecurity communication is a balance of compassion and common sense, listening and leading. People want to be safe online, but need realistic pathways to get them there.
No matter how strong your security stack is, human behavior and psychology still have a critical role in keeping things secure. That’s why giving people a clear, actionable game plan instead of murky marching orders does more to build a strong security foundation than any printed training certificate ever could.