In a world where cyber threats evolve at a blazing-fast pace, relying solely on reactive measures isn’t enough.
Enter: threat hunting, a proactive approach that uses threat intelligence, alerts, and log data—or even technical experience—to create and define hypotheses that can be tested to find unknown threats, security gaps, and potential zerodays.
As cyber threats become more sophisticated, threat hunting empowers businesses to seek out and neutralize threats before they can cause significant damage. Our cybercrime report revealed that 58% of businesses lost at least $100,000 from cybercrime in 2025, proving that proactive measures are more important than ever.
Keep reading to learn more about what threat hunting is, how it works, and why it matters.
What is cyber threat hunting?
Threat hunting is the proactive search across networks and endpoints to identify signs of malicious activity often missed by traditional security defenses. Unlike conventional security measures, which rely on alerts triggered by known threats or vulnerabilities, threat hunting happens before the threat goes down.
It involves asking critical questions and testing hypotheses about potential threats based on observed behaviors or patterns. Think of it as spotting the smoke before the fire—catching early indicators of compromise before they turn into full-blown incidents.
Threat hunting vs. threat detection vs. threat intelligence
These three practices—threat hunting, threat detection, and threat intelligence—are different, but each has an essential role in modern cybersecurity strategies. At a high level, threat hunting is proactive, threat detection is reactive, and threat intelligence provides the context and data that make both more effective.
Here’s an overview of their differences and similarities:
|
Threat hunting |
Threat detection |
Threat intelligence | |
|
Main goal |
Find hidden, unknown threats that have bypassed automated defenses |
Identify known malicious activity and generate alerts |
Provide context and knowledge about external and emerging threats to inform defenses |
|
Approach |
Proactive, human-driven |
Reactive, automated |
Analytical, research-based |
|
Input/triggers |
Alerts from security tools (SIEM, EDR, IDS/IPS) |
Hypothesis, threat intelligence reports, or hunches based on internal context |
Raw data, OSINT, dark web, security vendor feeds, internal hunting findings |
|
Output |
New detection rules and new threat intelligence |
Security alerts, incident creation |
Actionable reports and feeds |
|
Timing |
Periodic or continuous |
Real-time or near real-time |
Continuous collection and analysis |
|
Key tools |
SIEM querying, EDR, network analysis tools, custom scripts |
SIEM, EDR, IDS/IPS, antivirus |
Threat intelligence platforms (TIPs), OSINT tools, feeds, and databases |
How threat hunting works
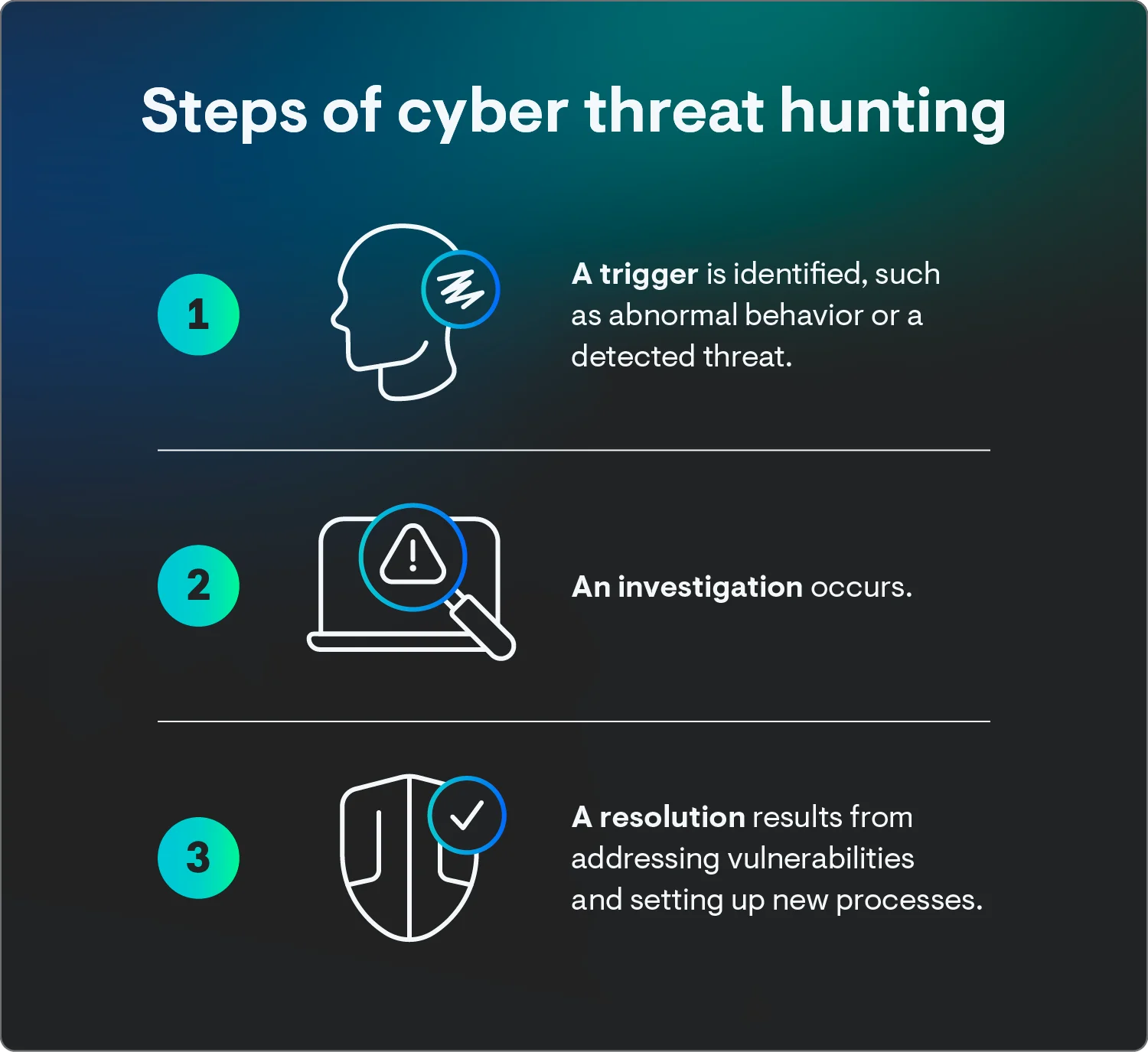
The threat hunting process is proactive, so it can start at any time. Here’s a brief look at how it works, in most cases:
-
Trigger: The hunt starts by identifying a trigger—this may come from alerts generated by security tools like SIEM (Security Information and Event Management) systems, or from abnormal network behaviors.
-
Investigation: The next phase involves deep investigations to analyze the gathered data, using analytics and potentially machine learning tools for pattern recognition and anomaly detection.
-
Resolution: Finally, once the hunter finds proof, it's time to act—patch vulnerabilities, update security policies, and remove malicious artifacts so the threat doesn't come back.
Types of threat hunting
All types of cyber threat hunting fall into two main categories: structured or unstructured.
-
Structured threat hunting is the more common and potentially more efficient approach as a specific goal of figuring out these threats. The hunter has an idea of the tactic, technique, or procedure (TTP) they’re looking for.
-
Unstructured threat hunting is data science applied to security. It’s driven by hypothesis, but it's necessary because advanced attackers often employ never-before-seen techniques that bypass existing rules and known TTPs.
Threat hunting methodologies
Everyone has their own approach or way of thinking about things, and that goes for researchers, too. While there are two main types of hunts, there are also four hunting methodologies:intelligence-driven, data-driven, knowledge-driven, and hybrid hunts.
1. Intelligence-driven hunts
Intelligence hunting is a structured hunt that involves collecting and analyzing intelligence from various sources to execute the hunt mission. Intel can consist of file names, hashes, IPs, campaigns, IOCs, email addresses, domains, etc. Using the collected intelligence, we can create hypotheses to test against internal data sources.
2. Data-driven hunts
These unstructured hunts rely on internal data that could potentially indicate malicious behavior. The types of data often include low-priority alerts, detections,or aggregated analytics.
This data does not give us our “smoking gun,” nor does it mean anything bad is happening at all, but it gives us a good starting point to create hypotheses on what we’re seeing.
3. Knowledge-driven hunts
Knowledge-driven hunts rely on our knowledge of available data sets, client networks, and adversary TTPs. Knowing adversary TTPs lets us identify and recognize potential threat behaviors. Using frameworks like MITRE ATT&CK, we can create hypotheses based on threat actor TTPs that have been seen in the wild.
4. Hybrid hunts
Hybrid hunts combine two or more types of hunts, which can help us create hypotheses with a narrower scope. For example, if data shows certain events happening on endpoints and intel suggests that these events could be part of a campaign that adversaries are conducting, we can create a hypothesis that combines both data-driven and intelligence-driven approaches.
Threat hunting best practices
When threat hunting, there are some good ways to do things and some… less good ways to do things. Here's how to make sure you’re doing things the good, good way:
-
Know your environment: Understanding what "normal" looks like in your network helps identify anomalies that signal threats.
-
Use threat intelligence: Incorporate intel feeds to stay informed about current threat landscapes.
-
Engage continuous learning: Threat landscapes evolve—regular training and knowledge updates for your threat hunting team are essential.
-
Foster an adversarial mindset: Encourage hunters to be curious, skeptical, and to actively "think like the attacker." Adopt an “assume breach” mindset.
-
Develop diverse skills: A successful hunter needs a mix of skills: data analysis, network forensics, malware analysis, and often scripting/coding (Python, PowerShell) to automate repetitive tasks and create custom tools.
-
Dedicated time and resources: Threat hunting should be a defined, scheduled activity, not something analysts do if they have free time. The most mature programs have dedicated hunt teams.
-
Automate successful hunts: If a hunting query successfully finds a threat, the goal is to "Hunt Once, Detect Forever." The successful query should be immediately translated into a new, automated detection rule in the SIEM or EDR (Endpoint Detection and Response), freeing the hunter to focus on the next unknown threat.
Threat detection tools
Every hunter needs a good set of tools for a successful hunt. Here are some commonly used threat detection tools:
-
Security Information and Event Management (SIEM): HuntressManaged SIEM brings enterprise-grade SIEM capabilities to any threat hunting team, centralizing logs and alerts from across your environment so that potential incidents can't hide in the noise.
-
Endpoint detection and response (EDR): Get the upper hand against threat actors with either managed or unmanaged endpoint protection that focuses on tracking and analyzing activities on endpoints to detect malicious behavior.
-
Threat intelligence platforms (TIPs): Aggregate threat data from multiple sources—valuable for both proactive and reactive measures.
Why threat hunting matters
At the end of the day, software can't out-think a human. Machine learning and automation have their place, but they still require humans to make the last-minute decision to contain and respond accurately.
And modern threat actors are smart and know how to exploit those blind spots. They’ve got entire teams that spend their days identifying ways to abuse, exploit, or slip past IT security tools. How can you expect to beat that with automation alone?
That's why we need hunters on the front lines. A threat hunter with a well-trained eye is more likely to pick up on TTPs and suspicious activity and can actually help software-based tools be more accurate. Overall, threat hunting enables security teams to identify unknown threats and catch them before they cause major damage and disruption.
Leave the threat hunting to Huntress
As we’ve seen threat actors working nonstop, we’ve also seen threat hunting become an essential part of modern defense. If you think about it, attackers have the first-move advantage in most scenarios—their victims aren’t even aware of their presence until it’s too late.
Threat hunting helps close that gap. Human-powered threat hunting is all about being proactive, combining technical and behavioral analysis to help businesses stay ahead of the latest threats and catch them before they can do more damage.
Huntress Managed SIEM uses proprietary Smart Filtering technology that only captures the data you need and cuts through all the noise. Our 24/7 expert-led monitoring helps you find and wreck elusive hackers.
Learn more about Huntress Managed SIEM, and happy hunting!
FAQ
What is the main objective of threat hunting?
The main objective of threat hunting is to proactively search for and identify hidden, unknown malicious activity that slips past existing automated security controls and detection systems.
What is the difference between SOC and threat hunting?
The security operations center (SOC) is the central, general-purpose team responsible for monitoring, detecting, analyzing, and responding to known security incidents reactively. Threat hunting is the human-driven, proactive discipline within the SOC focused on searching for unknown and persistent threats that have evaded the standard automated SOC tools.
What are four main types of threats?
Cyber threats are usually divided into four main types: malware, social engineering, network attacks, and application or web attacks.