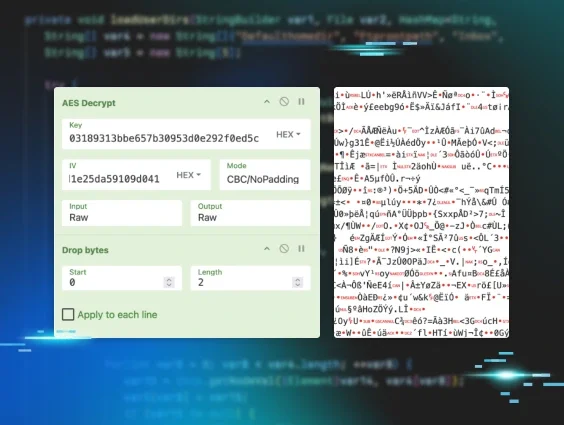
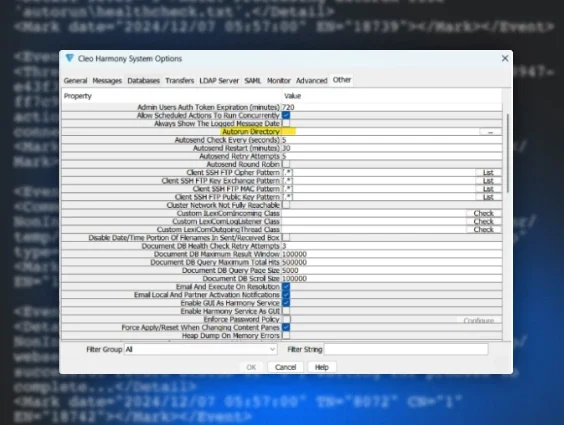
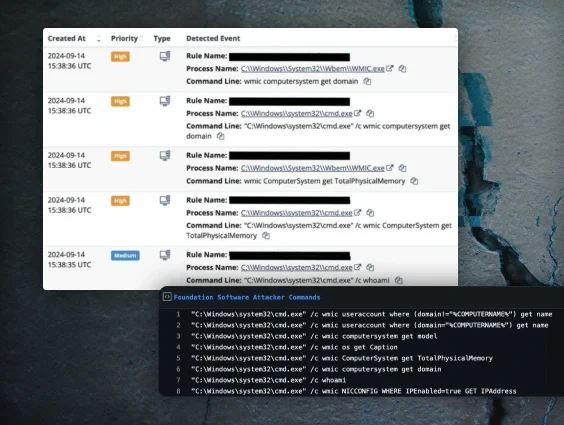
PeerBlight Linux Backdoor Exploits React2Shell CVE-2025-55182



Response to Incidents
Be the first to know about CVEs and threat advisories that we're seeing on the front lines. We'll break down how these threats or attacks work, do in-depth analysis, and provide mitigation guidance.



Browse Categories
+ View AllSign Up for Huntress Updates
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
Thank you! Your submission has been received!
Add Cyber Experts to Your Arsenal
See how the global Huntress SOC can augment your team with 24/7 coverage and unmatched human expertise. Start your free trial today.